In-depth security trends and strategies against DDoS attacks in 2024
Fri Mar 15 2024
The year 2023 witnessed a worrying surge in the frequency and sophistication of DDoS attacks worldwide. This has prompted significant concerns about the current cybersecurity landscape, highlighting the critical importance of implementing advanced DDoS defense strategies. Join VNETWORK as we analyze the notable shifts in the ongoing battle against DDoS attacks in 2023 and provide insights into anticipated cybersecurity trends for 2024.
Overview of DDoS attack landscape in 2023
Distributed Denial of Service (DDoS) attacks continue to pose one of the most significant cybersecurity threats in the current landscape. These attacks have the potential to disrupt even the most robust information systems by inundating servers with massive volumes of traffic, resulting in service outages, data loss, and substantial financial and reputational harm to businesses. Here are some notable insights into the state of DDoS attacks in 2023 and the potential trends for further development in 2024.
Large-scale DDoS attacks
According to Cisco's projections, there has been a sharp increase in DDoS attacks globally, doubling from 7.9 million incidents in 2018 to 15.4 million incidents in 2023. These projections are based on frequency analysis data up to 2020 and extrapolate predictions for the subsequent three years. This surge underscores a significant challenge in the cybersecurity domain, prompting enterprises to bolster their defenses against the growing threat landscape.
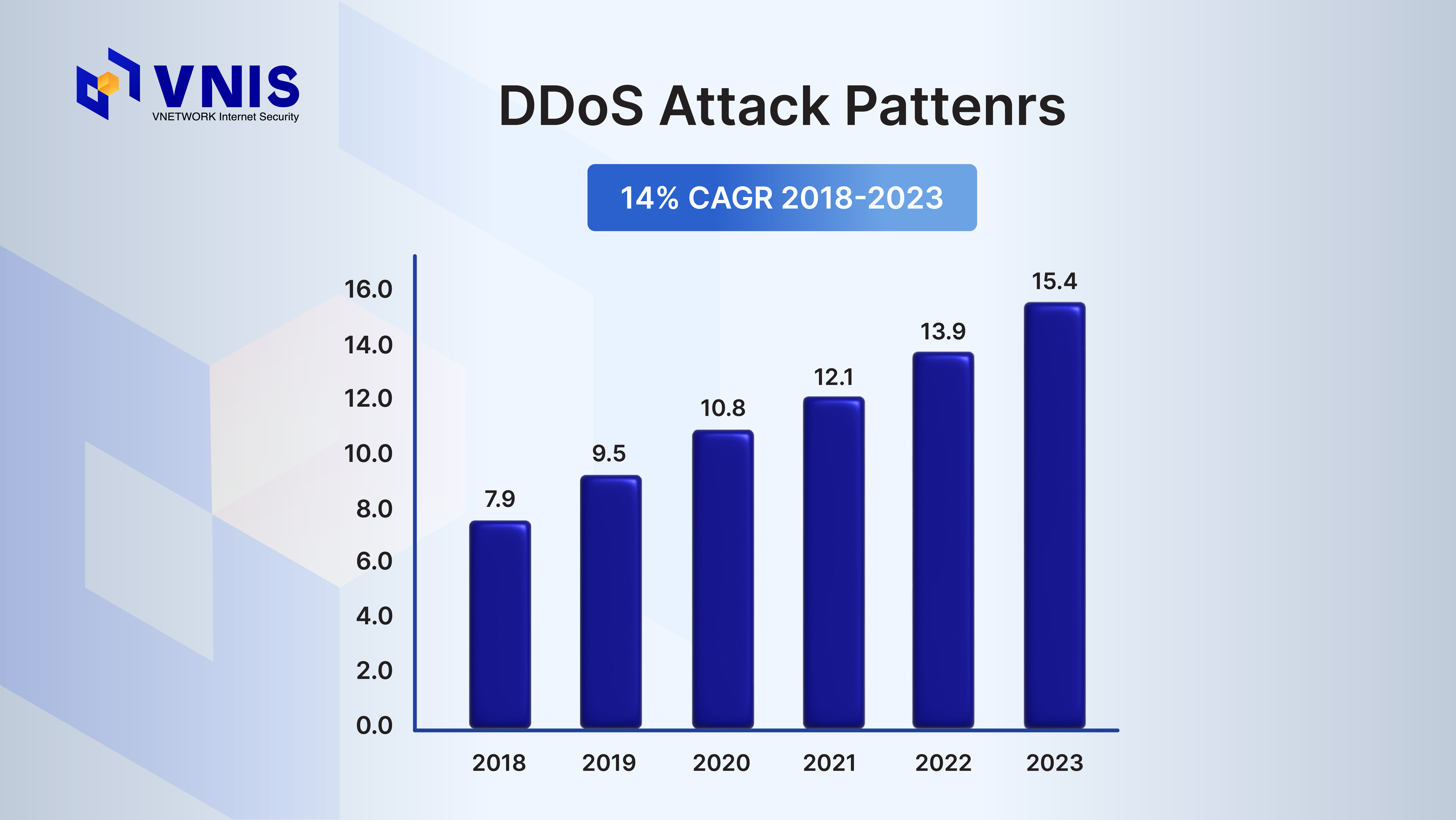 The scale of DDoS attacks over the years
The scale of DDoS attacks over the years
Sophisticated attack methods
The era of using simple botnets to flood servers with a barrage of requests has evolved. Presently, hackers are orchestrating more intricate attacks by leveraging:
- IoT Device Exploitation: These botnets exploit security vulnerabilities in household and office smart devices to form vast networks, amplifying the attack power.
- Cloud Infrastructure: Attackers leverage the flexibility and scalability of cloud platforms to execute distributed, difficult-to-trace attacks.
- Protocol Vulnerability Exploitation: By exploiting weaknesses in communication protocols, attackers can bypass conventional defense measures and cause significant damage.
Targeted DoS/DDoS attacks
The rise of targeted DDoS attacks serves as a warning bell for enterprises. Throughout 2023, DDoS attacks exhibited alarming developments:
- Increased frequency: The number of DDoS attacks continued to rise steadily, indicating escalating risks for global enterprises.
- Prolonged duration: Unlike previous short-term attacks, DDoS incidents can now last for hours, even days, causing severe disruptions and substantial damage.
- Enhanced sophistication: Attackers are employing more complex techniques, combining multiple attack vectors simultaneously (multi-vector attacks) to overcome traditional defense measures.
- Multi-targeting: Instead of targeting a single IP address, DDoS attacks nowadays often strike multiple horizontal targets simultaneously in the same event, augmenting attack potency and complicating defense efforts.
Impact of DDoS attacks on businesses
DDoS attacks can have severe repercussions for businesses, including:
Service disruption
This is the most evident impact of DDoS attacks. When a target is under DDoS attack, it becomes unable to fulfill legitimate requests from users. This can lead to customers being unable to access the business's website, applications, or services, resulting in revenue loss, damage to reputation, and erosion of customer trust.
Reputation damage
DDoS attacks can tarnish a business's reputation in various ways. When customers cannot access the business's services, they may feel neglected or disregarded. This can lead to reduced revenue and customer loss. Additionally, when a business falls victim to a DDoS attack, it may signal to customers that the business is unable to protect its systems, leading to loss of credibility and customer trust.
Data breaches
In some cases, DDoS attacks can be used as a smokescreen to conceal other malicious activities, such as intrusion and data theft. When attackers gain control of a business's network system, they can access sensitive data, such as customer information, financial data, or proprietary information.
Infrastructure damage
DDoS attacks can disrupt all or part of a business's infrastructure. This includes interrupting the operations of servers, networks, web services, and applications, affecting users' ability to access and use them. Moreover, DDoS attacks incur significant costs and resources for businesses in mitigating the damages and consequences of these attacks.
Security trends against DDoS attacks in 2024
In the face of continuously evolving and sophisticated DDoS threats, both enterprises and cybersecurity professionals are confronted with significant challenges in proactively addressing and mitigating these attacks. The pivotal question arises: How can service providers adapt to the rapidly changing landscape of DDoS attacks? Below are predictions regarding the evolving trends of DDoS mitigation solutions in 2024:
Cloud-based DDoS defense
With the escalating scale of DDoS attacks, a strategic shift towards cloud-based defense mechanisms emerges as a preferred approach, owing to its inherent flexibility, scalability, and cost efficiency.
Key Advantages of Cloud-Based Solutions:
- Unlimited Scalability: Cloud-based DDoS defense platforms boast unparalleled scalability, allowing them to seamlessly expand to combat volumetric attacks that far exceed the capacities of traditional on-premises solutions. Leveraging cloud resources such as virtual servers, networks, and storage, these solutions can dynamically adjust to fluctuating traffic demands, ensuring optimal performance even during peak attack periods.
- Global Distribution: Cloud-based defenses leverage distributed architectures spanning multiple geographic regions, effectively dispersing and mitigating attack traffic across a network of strategically positioned mitigation nodes. By leveraging content delivery networks (CDNs) and edge computing capabilities, these solutions can efficiently absorb and neutralize DDoS attacks at the network edge, minimizing their impact on targeted systems and services.
- Cost-Effectiveness: Cloud-based DDoS mitigation offers a cost-effective alternative to traditional on-premises solutions, particularly for small and medium-sized enterprises (SMEs) seeking to bolster their defenses without incurring prohibitive infrastructure investments. By adopting a subscription-based pricing model, cloud service providers offer flexible and scalable solutions that align with the evolving needs and budgets of businesses, enabling them to optimize their cybersecurity posture while minimizing operational overheads.
Application of Artificial Intelligence (AI) and Machine Learning
The technology of AI and Machine Learning is widely applied across various industries, including cybersecurity. In the realm of DDoS attack prevention, AI and Machine Learning are utilized to:
- Traffic Analysis: AI and Machine Learning technologies can be employed to analyze network traffic, identify anomalous attack patterns, and automatically trigger countermeasures. This surpasses the capabilities of traditional manual responses, enabling systems to swiftly and effectively detect and prevent DDoS attacks.
- Automation: AI and Machine Learning technologies can automate security tasks such as detection, analysis, and response to DDoS attacks. This helps minimize reliance on human intervention, optimize response speed, and save costs.
Multi-Layered, Multi-Vector attack defense
DDoS attacks are increasingly sophisticated, combining multiple attack forms simultaneously. Therefore, to enhance protection effectiveness, DDoS mitigation solutions need to be capable of combating multi-layered, multi-vector attacks. In this regard, multi-layered defense involves utilizing various defense layers to thwart DDoS attacks. These defense layers may include:
- First-Line Defense: Simple, easily deployable defense measures such as IP filtering, MAC address filtering, or port filtering. These measures can help prevent basic DDoS attacks, such as IP or MAC spoofing-based attacks.
- Second-Line Defense: More sophisticated defense measures, such as AI or Machine Learning-based traffic filtering systems. These measures can help detect and prevent more sophisticated DDoS attacks, such as botnet-based attacks or attacks using stealth techniques.
- Third-Line Defense: Final defense measures, such as traffic redirection systems or Intrusion Detection and Prevention Systems (IDS/IPS). These measures can help minimize the impact of DDoS attacks that have bypassed the first and second defense layers.
VNIS - Comprehensive security solution for enterprises
To address businesses' growing concerns about increasingly sophisticated and complex DDoS attacks, VNETWORK has unveiled the VNIS (VNETWORK Internet Security) comprehensive web/app/API security solution. With the ability to effectively handle DDoS attacks of up to thousands of Tbps while ensuring stable system operations, VNIS is committed to providing customers with peace of mind in safeguarding their systems against all network attacks. VNIS aids in ensuring the security of enterprise web, app, and API applications, offering the following features:
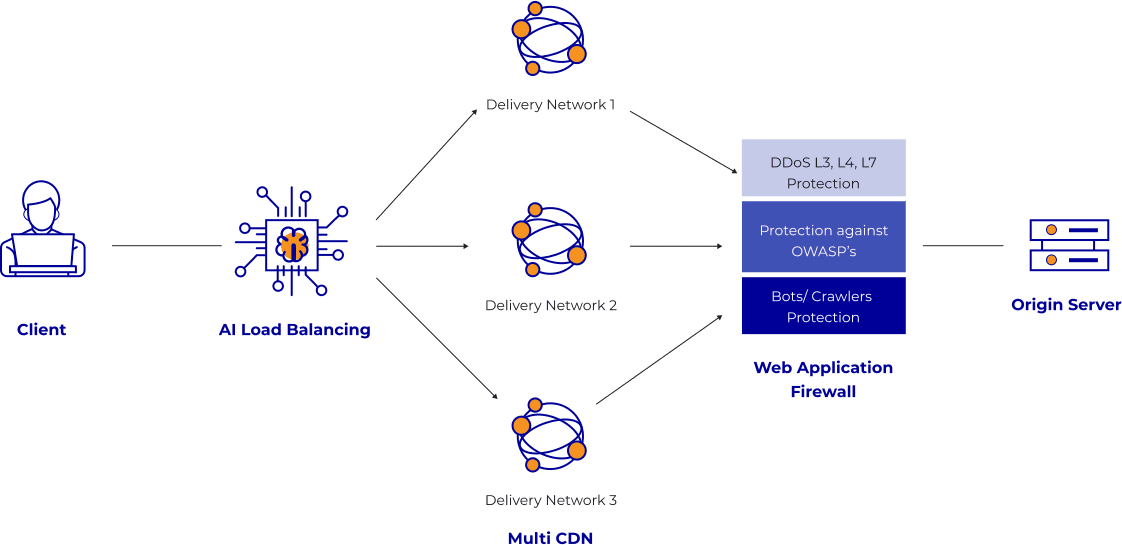 VNIS comprehensive security model
VNIS comprehensive security model
Robust CDN system
The Multi-CDN system within the VNIS platform boasts a capacity to handle loads of up to 2,600 Tbps, enabling enterprise websites/apps/APIs to operate smoothly against any DDoS attacks, regardless of traffic. Specifically, in Vietnam, VNETWORK's VNCDN system can accommodate over 5 million simultaneous users and process over 8 billion requests per day, ensuring readiness and stability for enterprise systems in any attack scenario.
Layer 7 attack prevention with Multi-Cloud WAF and Scrubbing Center
In the battle against DDoS, VNIS also focuses on preventing exploitation at Layer 7 (application layer). The VNIS platform equipped by VNETWORK with Multi WAF features multiple global Cloud WAF clusters, leveraging dense cloud infrastructure to swiftly isolate threats when website traffic spikes occur. Accompanying this is a network monitoring system for WAF (Scrubbing Center) that coordinates the operations of Cloud WAF clusters in various countries, enhancing the effectiveness of Layer 7 DDoS defense.
Performance optimization with AI Smart Load Balancing system
Utilizing advancements in Artificial Intelligence, VNETWORK has developed an intelligent Load Balancing system (AI Load Balancing) combined with Real User Monitoring (RUM) capabilities. This system analyzes detailed attack sources, reports real user interactions with the website, automatically detects the shortest path between the server and users, and swiftly routes traffic.
IPs concealment and Server Root protection
The VNIS platform allows enterprises to customize connections, inspect, and conceal server IP addresses within a single management platform, with simple execution and no requirement for high-level programming expertise.
Expert team and 24/7 SOC support
Recognizing the urgency and importance of security matters, VNETWORK has established Security Operation Centers (SOC) with a readiness spirit to combat emergency situations and minimize losses. Currently, VNETWORK's SOC system operates in Vietnam, Singapore, and many other countries, assisting enterprises in monitoring and immediately responding to network attacks.
Conclusion
With the VNIS solution - a comprehensive and effective Web/App/API security platform, businesses can rest assured in developing their operations as their information systems are fully protected against all potential attack risks. For detailed consultation and pricing, please contact VNETWORK using the following information:
- Hotline: +84 (028) 7306 8789
- contact@vnetwork.vn
Table Of Contents